- How Do Phishing Scams Work?
- Red Flags of Phishing Scams
- How to Beat Phishing Scams
- What To Do If You Fall Victim to a Phishing Scam
- Frequently Asked Questions
Anyone who uses email, the internet, and even a phone can be a target for phishing scams, and the consequences can be severe. Once you have been tricked into handing over your sensitive information, you could quickly become the victim of financial loss and identity theft.
What is Phishing?
A technique used by cybercriminals to steal sensitive data—like financial accounts, login details, or personal information—by impersonating genuine companies or individuals.
Learning to recognize phishing scams will help you stay one step ahead of the fraudsters and to mitigate the damage if the worse happens.
How Do Phishing Scams Work?
Phishing occurs when a scammer masquerades as a legitimate company or genuine person to steal personal data. Most phishing scams target you through email, but they can also be initiated through social media, phone calls, and text messages.
Scammers use public sources of information to gather information on their potential victims. For example, by browsing social media networks, like LinkedIn, Facebook, and Twitter, scammers can uncover things like your:
- Name
- Occupation
- Place of work
- Email address
- Date of birth
- Address
This information can then be used to create a believable and genuine-looking email or impersonate someone else over the phone or text message.
Most phishing emails use one of two basic methods:
- Malicious attachments, which usually have enticing names, such as ‘INVOICE’ or ‘CONTRACT.’ When the attachment is opened or downloaded, malware is installed on your machine, which gives hackers remote access to your computer.
- Malicious links to websites, which are often clones of legitimate ones to appear genuine, where you are prompted to enter your login details. Alternatively, once you click through to the website, malware is downloaded onto your device.
Phishing Scam Example
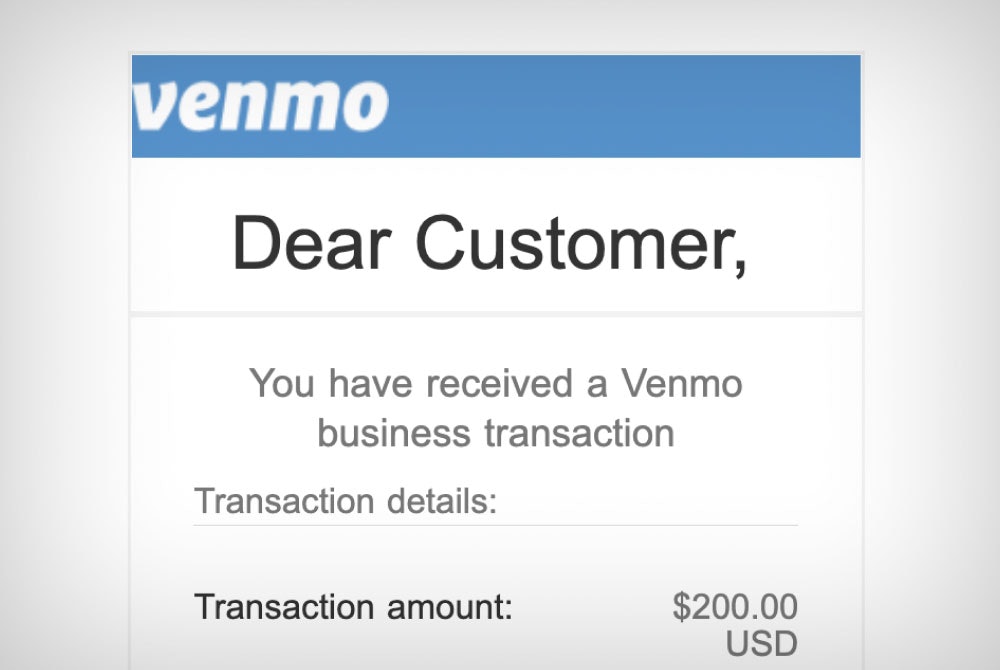
You receive an email from Netflix that says you need to update your payment details, and your account will be on hold until you do.
The email features the real company logo, uses your name, and at first glance, the sender's email address tells you it’s from ‘Netflix.’
You’re invited to click a link to update your payment details, which takes you to a webpage that appears to be a genuine Netflix one.
Not wanting to miss the next episode of Ru Paul’s Drag Race, you enter your payment details into the fields provided.
YOU’VE JUST BEEN SCAMMED!
Your information has just been sent to the scammer, and they now have access to your accounts, money, and maybe more.
Phishing scammers use a variety of tactics in their emails to fool you into opening an attachment or clicking on a link, including:
- Claiming there’s a problem with your payment details
- Saying they’ve noticed suspicious activity or login attempts
- Requesting you confirm some personal information
- Asking you to click on a link to pay an urgent invoice
- Telling you you’re able to register for a tax or other government refund
- Offering you a coupon for free stuff or telling you you’ve won a prize
Red Flags of Phishing Scams
Your email spam filter will keep many phishing emails out of your inbox. However, the more sophisticated scammers can slip past your spam filter. So, how do you know that an email is a scam or legit? There are a few warning signs to look out for:
- Bad grammar, spelling, and punctuation.
- Misspelled domain names or shortened domain links.
- Unusual email addresses (e.g., an email from Microsoft or Netflix using an @gmail.com email).
- Alarming content full of warnings or threats of action from the authorities.
- Asking for personal information, such as login credentials or bank details, which you should never give out online, unsolicited.
- A sense of urgency (e.g., your account has been blocked, one of your policies is expiring, or a deal is ending very soon).
- An offer that is too good to be true.
- An email claiming you’ve won a prize in a competition that you didn’t enter.
Most Commonly Impersonated Brands
In the first quarter of 2022, the most commonly impersonated brands in phishing attacks were:
- LinkedIn (52%)
- DHL (14%
- Google (7%)
- Microsoft (6%)
- FedEx (6%)
- WhatsApp (4%)
- Amazon (2%)
- Maersk (1%)
- AliExpress (0.8%)
- Apple (0.8%)
How to Beat Phishing Scams
Phishing scams are becoming more sophisticated, so it’s a good idea to put some extra protection in place to protect your accounts and your sensitive information. These are our top tips:
- Use antivirus software and keep it up to date. Also, set the operating software for your devices to update automatically, which can give you essential protection against security threats.
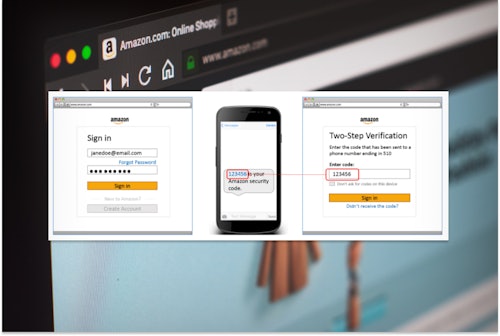
- Add multi-factor authentication to your accounts where possible. This provides an extra layer of security to your account, making it hard for scammers to hack into your account, even if they have your username and password.
- Back up important data using a secure cloud service or external drive that isn’t connected to your home network. Back up the data on your phone too.
- Only visit secure sites, i.e., websites with ‘https’ or a padlock icon at the beginning of the web address in your browser.
- Install a security add-on on your browser, which will run checks on the websites your visit and prevent you from visiting malicious ones.
- Use both network and desktop firewalls which act as a buffer between your device and outside threats. Using the two types of firewalls together significantly reduces your risk of a phisher hijacking your computer.
- Beware of pop-ups that often imitate genuine components of a legitimate website, for example, informing you that you’ve won a prize and need to add your details. The major browsers have settings that allow you to block pop-ups. However, if one does slip through, click the small “x” in the upper corner of the window to close it and nothing else to make sure you don’t get redirected to a phishing site.
- Use unique passwords for all of your accounts. This way, if a scammer gets hold of your password, they won't gain access to everything. Use a password manager, so you don't have to remember all of your passwords.
Phishing Stats
- 96% of phishing attacks arrive by email
- As of Jan 2021, Google has registered over 2 million phishing websites
- According to the FBI, Phishing was the most common type of cybercrime in 2020
What To Do If You Fall Victim to a Phishing Scam
Phishing scams are becoming more sophisticated, so you may not realize right away that an email is fraudulent. If you do think you’ve been caught in a phishing scam, here are the steps you can take to safeguard your compromised data and protect yourself in the future.
1. Don’t Panic
Don’t beat yourself up, and don’t panic. Falling for a phishing scam doesn’t automatically mean your identity will be stolen. Phishing scams vary, and your next steps are dependent on what kind of phisher targeted you.
If you:
- Downloaded a fraudulent attachment: Turn off the WiFi and disconnect from the internet immediately to remove the scammer’s access to your computer.
- Clicked through to a fraudulent website: Note down all the information you entered into the website. Take screenshots of both the website and email.
2. Change Your Passwords
As soon as you’re able, change your passwords, password hints, and security questions to all of your online accounts. If you don’t already, use a password manager to generate strong, unguessable passwords and store them behind a robust wall of encryption.
3. Check Your Accounts
Go through your financial accounts and check if any unauthorized purchases have been made. Also, look at your email and social media profiles to ensure that they haven’t been hacked—check to make sure unknown messages haven’t been sent from your account.
4. Contact Organizations
Contact the organizations associated with affected accounts to let them know that you’ve been a victim of a phishing scam and that your identity has been stolen. For example, if you’ve lost financial information, you’ll need to cancel your cards and report fraudulent transactions.
5. Check for Viruses
Whether you clicked on a link or downloaded an attachment, scan your devices for viruses and other malware. If your anti-virus software finds any infected files, remove them immediately and then scan again to ensure the threat has been neutralized. In addition, help prevent malicious files from being uploaded to your devices by keeping your antivirus and device software updated.
6. Check for Signs of Identity Theft
Monitor your bank and credit card statements for unauthorized purchases or withdrawals, and ask your bank to alert you to any unusual activity. Next, notify the three credit agencies that your identity may be compromised and order your credit reports to check new accounts haven’t been opened in your name.
7. Report the Phishing Scam
If you suspect your identity has been stolen, report it to the Federal Trade Commission (FTC) and other authorities who will guide you through the next steps. Also, place fraud alerts on your credit reports to make it difficult for scammers to open lines of credit in your name.









Comments