- Quick Email Verifier Checklist
- 8 Ways to Verify an Email: Genuine vs. Scam
- How to Protect Yourself from Scam Emails
- Frequently Asked Questions
An unofficial sender email address, urgent requests for personal information, redirect links that don’t match the anchor text, spelling and grammar errors, and unexpected attachments are all big red flags that you’re looking at a scam email.
Never respond to requests for personal information via email, even if there are threats of harm. Instead, contact the organization directly for verification, using the contact details found on the legitimate website or your paper statements, etc.
Protect yourself from phishing attempts by never clicking on links or downloading attachments in emails, adding two-factor authentication to your accounts, keeping security software up to date, and use strong and unique passwords for all your online accounts.
Quick Email Verifier Checklist
If you answer yes to these questions, the email is likely safe:
- Does the email address match the company's owned domains?
- Was the email sent only to you? (Versus being Bcc'd.)
- Do the links in the email go to the company's legitimate website?
- Is the email free from spelling mistakes and grammatical errors?
The following are all signs of a scam. If you receive an email with any of these elements, be sure to verify that it's real before clicking on any links, providing any information, opening attachments, or sending any money:
- An email asking for personal information.
- An email containing threats or a sense of urgency.
- A strange email from someone you know asking for money.
8 Ways to Verify an Email: Genuine vs. Scam
If you fail to recognize an email as a phishing attack, a scammer masquerading as a representative of a well-known organization could trick you into handing over your details.
Once a scammer has your personal information, they could drain your financial accounts, make unauthorized credit card purchases, open new lines of credit in your name, or use your social media or email accounts for criminal activity.
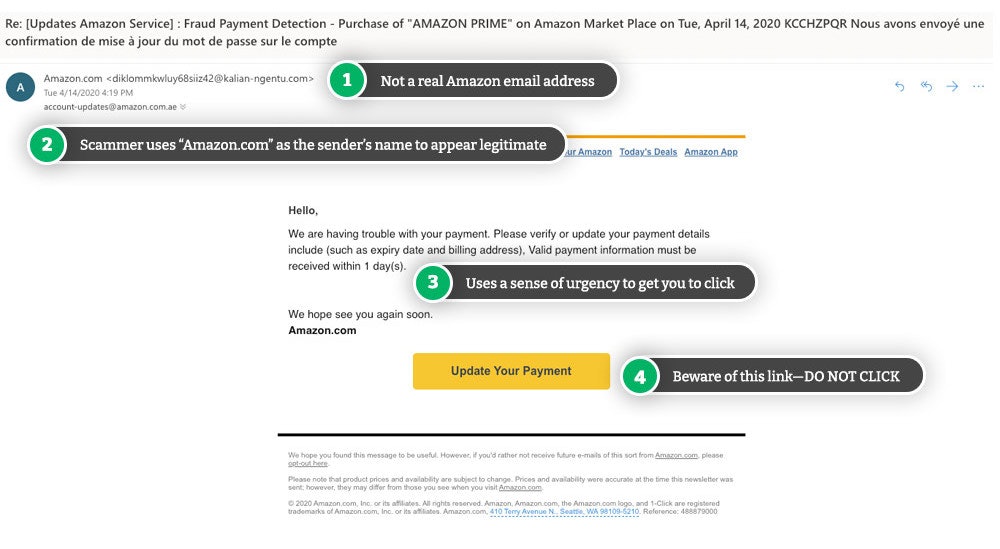
1. Look at the Sender’s Address
The display name in an email can be anything the sender chooses it to be, so just because an email pops into your inbox from ‘Netflix’ doesn’t always mean that’s the case.
To verify who sent the email, check the sender’s full email address. It could be a phishing scam if:
- The alleged company name is misspelled
- The sender’s email is coming from public domain email addresses like Gmail and Hotmail. Large companies use their domain names in an email.
- It’s a cousin domain, i.e., a look-a-like domain that can fool people by being close to a genuine business email address (e.g., paypa1.com).
- The email address doesn’t match the address from previous emails from the organization you know to be genuine.
- The display name and the name in the email address don’t match.
Commonly Impersonated Organizations in Email Scams
| Organization | Genuine Website | Genuine Email/Domain |
| Amazon | https://www.amazon.com/ | |
| Apple | https://www.apple.com/ |
@email.apple.com |
| DHL | https://www.dhl.com/ |
@dhl.com |
| https://www.google.com/ |
@google.com |
|
| https://www.facebook.com/ |
@facebookmail.com |
|
| Microsoft | https://www.microsoft.com/ |
@microsoft.com |
| Netflix | https://www.netflix.com/ |
[email protected] |
| PayPal | https://www.paypal.com/ |
@paypal.com |
| Robinhood | https://robinhood.com/ |
@robinhood.com |
| Social Security Administration | https://www.ssa.gov/ |
[email protected] |
2. Check For Strange Uses of the Bcc Field
If you find your address in the blind carbon copy (Bcc) box instead of the recipient box, it’s a red flag that something is wrong. The Bcc box is primarily used for sending an email to multiple recipients, but any recipients added to the box will not be shown to any other recipients who also receive the message.
Genuine companies would correspond with you directly, so if your name is in the Bcc field, it could indicate that a scammer has sent the email to multiple email addresses, but they don’t want you to know that. Think about it, why would an email relating to your account be potentially sent to other recipients?
3. Is the Email Asking for Personal Details?
If an email is asking you to update personal details like your Social Security number (SSN), bank account numbers, your date of birth, or answers to security questions, you’re probably looking at a scammer. Legitimate companies will rarely ask for your sensitive information via email.
4. Investigate Unexpected Embedded Links
Another characteristic of a fake email is unexpected, embedded links. Scammers will embed links in text that will appear to take you to a genuine website. However, if you take that on trust and click on the link, you could download dangerous malware onto your device without knowing or be taken to a phishing website.
The website will likely be a clone of a genuine site—,enter your details into it, and you’ve just handed them over to a scammer. You should also be aware that some malicious redirects are also hidden in the “unsubscribe” link.
How to Check Email Links
There are two main ways of checking if a link is legitimate:
- Hover your cursor over the link to display the full URL. This shows you where you’ll be redirected to. If the URL doesn’t match the linked text or is a strange, long URL, it’s probably a dangerous link.
- Right-click on the link and select “Inspect.” The pop-up window will show the code for the email, including the full URL.
A common tactic of scammers is to use shortened URLs in their embedded links. You can recognize these links as they usually start with tinyurl, goo.gl, bit.ly, t.co, etc. Enter the shortened link at getlinkinfo.com to see the expanded URL.
4. Check for Spelling and Grammar Errors
Genuine companies have teams of people working on communications, including email correspondence, and therefore, follow strict copywriting and editorial standards. So, while minor typos may happen, it’s rare to see multiple and glaring spelling and grammatical errors.
If the subject line and the main body of the email feature obvious spelling mistakes, misuse of punctuation, and poor grammar, it’s a big red flag that it’s fake.
5. Examine the Tone of the Email
Creating a sense of urgency is a key weapon in a scammer’s arsenal. They will try to trigger an emotional response—like, anger, shock, panic, or empathy—to trick you into doing what you usually wouldn’t (i.e., clicking on a link, downloading an attachment, or sending sensitive information).
Examples of the ways phishing scammers create a sense of urgency include:
- Claiming they’ve detected unauthorized activity on your account
- Threatening to suspend your account if you don’t update your details
- A receipt for an Amazon purchase you didn’t make
- Offering you an unbelievable deal or free products
- Telling you you’ve won a prize, like a free holiday
- Sending you a job offer
- Informing you there has been a data breach including your sensitive information
- Asking for a donation following a tragedy or a natural disaster
Scammers also usually impose a deadline for you to take action to increase your sense of urgency to encourage you to act without thinking. Perhaps you’ll miss out on a prize, lose access to your Netflix account, or have to answer to law enforcement.
What About the Greeting?
Fake emails will often address you as simply “Sir” or “Madam” because the same email has probably been sent to thousands of recipients in the hope a few will fall for the scam.
So, if an email is impersonal, not just in the greeting, but throughout with generic statements and vague details, it’s likely to be from a scammer.
6. Consider Attachments Carefully
When you see an attachment in an email, ask yourself if you were expecting this information. Scammers often add attachments to their phishing emails to entice you to download dangerous malware that could log your keystrokes or harvest your personal information without your knowledge.
Scammers label these attachments to pique your curiosity, such as:
- Invoice
- Receipt of Payment
- Contract
- Notice of Cancellation
- How to Claim Your Prize
Document-based malware has become common amongst phishers, so be wary if you receive an unsolicited email with an attachment.
7. Strange Messages From People You Know: Verify With the Sender
Can you trust an unsolicited email from a friend or relative when it comes from their genuine email address? You probably can, but it’s still important to be vigilant.
It’s possible your friend or relative has previously been the victim of a malware attack and their email account has been hijacked to send phishing emails to all their contacts. It can be harder to identify fake emails from your known contacts, but there will likely be something unusual about the content, such as:
- An urgent request for financial help
- The promise of great deals if you click the embedded link
- Asking you to download photographs or documents for them
- Asking you to help them raise money for a charity
- Telling you they’ve lost your phone number
If you get such an email, don’t respond, even if the email address is real. Instead, reach out to your friend or relative via phone call (not from a number in the email), or in person.
8. Check with the Real Company
If you’re still unsure if an email is a scam, get in touch with the organization or company that has allegedly contacted you. Visit the social media pages or official website to find genuine contact details and ask them to verify the request of the email.
If you determine the email is fake:
- Block the sender to prevent further phishing emails
- Report the email as spam to your email provider
- Delete the email and empty your trash folder
- Report the fake email to the company that is being impersonated and to the Federal Trade Commission (FTC)
How to Protect Yourself from Scam Emails
As well as following our step-by-step guide for verifying the emails that land in your inbox, there are also several ways to protect yourself from fake emails.
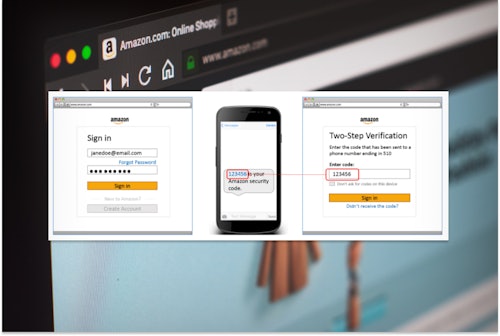
- Add multi-factor authentication to your online accounts where possible. This extra layer of protection makes it harder for scammers to hack into your accounts, even if you’ve unwittingly handed over your username and passwords.
- Use trusted antivirus software to protect you against malware and keep your operating software up to date for additional safeguarding against cyber threats.
- Check a Gmail message is authenticated. If you see a question mark next to the sender’s name, the message isn’t authenticated, meaning Gmail doesn’t know if the message has come from the person who appears to have sent it. If you see the question mark, proceed with caution.
- Install a security add-on on your browser which will warn you or block your access if you click on a link within an email that will redirect you to a malicious website.
- Use anti-spam filters. Only sign up for email accounts with providers that offer spam filtering to help prevent scammers from infiltrating your inbox.









Comments