- Steps to Take If You've Downloaded Malware
- Step 1: Disconnect From The Internet
- Step 2: Change Your Passwords
- Step 3: Remove Malware From Your Computer
- Step 4: Back Up Your Files
- Step 5: Review Your Financial Accounts
- Step 6: File a Report With the FTC
- Step 7: Contact the Impersonated Company
- Step 8: Stay Vigilant
- Frequently Asked Questions
Malware is a term used to describe any type of malicious software created by cybercriminals to harm or exploit any programmable device, service or network. Cybercriminals use malware to extract data such as financial information, personal passwords and emails, healthcare records and anything that can be leveraged for financial gain.
Nowadays, malware has become sophisticated enough that you may not even realize you've been infected until it's too late. If you think you’ve clicked on an unsafe link or downloaded a suspicious attachment in a malware attack, take these steps to protect your compromised data and prevent future attempts.
Steps to Take If You've Downloaded Malware
- Disconnect from the Internet
- Change Your Passwords
- Scan Your Computer for Viruses
- Backup Your Files
- Review Your Financial Accounts
- Report a Malware Attack with the FTC
- Contact the Company Being Impersonated
- Stay Vigilant & Monitor Your Accounts
Mobile Malware Attacks
If you think your smartphone may have been infected with malware, check out our guide to removing viruses from your iPhone or Android.
Step 1: Disconnect From The Internet
First thing’s first, take a few deep breaths to calm your nerves and remind yourself that it is going to be okay. You aren’t the first person to fall for a malware attack and won’t be the last.
Next, you’ll need to get your computer offline. If you’re using WiFi, open your network settings and disconnect. If you cannot locate your WiFi network settings, unplug your WiFi router from the wall or your cable box and turn it off.
How to Turn Off WiFi On a Mac
- Click the wireless icon in the upper left corner of the menu bar.
- Choose Turn Wi-Fi Off or toggle the blue button off so that the blue coloring no longer shows.
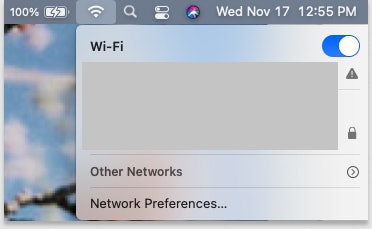
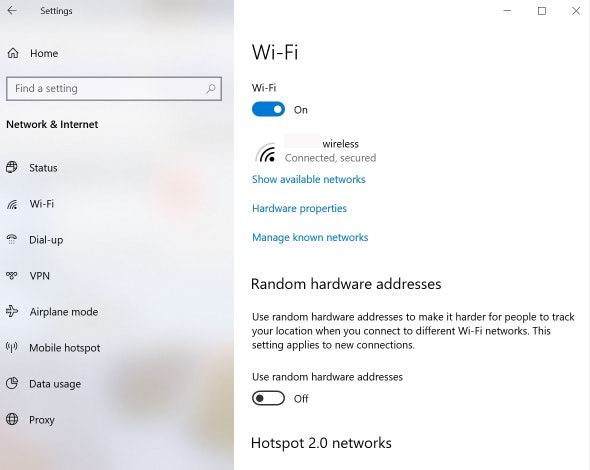
How to Turn Off WiFi On a PC
- Open Settings.
- Click the Network & Internet button.
- Click WiFi.
- Toggle the disconnect button to break the connection.
When using a wired connection, disconnect the ethernet cable from your computer immediately. This helps stop cyber attackers from gaining, or continuing to gain, remote access to your device. It can also prevent malware from spreading to other devices on the network.
Step 2: Change Your Passwords
Change your passwords quickly following a malware attack. This is especially true for sites that contain sensitive information (e.g., banking sites, healthcare accounts, Google credentials) and update any password hints or security questions.
Be sure to do so on a different laptop or via your phone and avoid changing them on the infected laptop. Also, avoid using the compromised WiFi network for internet access when logging into your accounts.
Follow these steps to create a strong password:
- Do not use sequential numbers or letters (e.g., 1234 or abcd).
- Never use your birth year, month or date in your password.
- Use a combination of at least eight letters, numbers, and symbols and toggle between upper and lowercase letters (e.g., LT#4brZ30q).
- Combine unrelated words using numbers and symbols as letter substitutes (e.g., 4F3nc3H0r53Bl0G).
- Don’t reuse your passwords.
Finally, consider a password manager so you don’t have to remember them all or keep them written down somewhere.
Password managers store your passwords in an encrypted digital vault which only needs one master password to be accessed. So you only need to remember one.
Typically, password managers allow you to sync your passwords to all of your devices and browsers, so they’ll auto-fill on the relevant sites and apps. It can also help you create unique passwords that are harder to crack, while some offer an auditing feature that checks for current weak and vulnerable passwords.
Step 3: Remove Malware From Your Computer
Run anti-virus software on your computer to be notified of any files that may have been infected with malware. If there are infected files, remove them immediately and perform a second scan to make sure they’ve been neutralized.
How to Check if Anti-Virus Is Already Installed
Microsoft and Apple both include built-in anti-virus software that comes standard when you purchase one of their computers. To check if your computer has this installed already, follow these steps:
If your computer is running Windows 8:
You’re in luck, you already have antivirus software installed. If Windows Defender is turned off, you will see a warning in the notification area on your taskbar. To make sure it is on, do the following:
- Go to Settings.
- Choose Windows Security.
- Click on Virus & Threat Protection.
- Click "Manage Settings" under virus & threat protection.
- Make sure all setting are turned on and you see a blue color.
If your computer is running Windows 7:
- Click Start button to access the Action Center.
- Click Control Panel, then System and Security, click Review your computer’s status.
- Click the arrow button next to Security to expand the section.
If your computer is running Windows Vista:
- Click the Start button to open the Security.
- Click Control Panel, then Security, and then Security Center.
- Click Malware Protection.
Windows doesn’t detect all antivirus software, so if you think you once installed protection but can’t find it, type the name of the software in the Search box on the Start menu. Next, look in the notification area of the taskbar to find the antivirus program’s icon.
If you’re using a Mac:
The only Apple operating system that needs antivirus software is macOS, all later versions automatically come with XProtect. To ensure your anti-virus software stays up to date, do the following:
- Open Finder.
- Click Applications.
- Click System Preferences.
- Click Software Update.
- This will automatically run a check to see if an upgrade is needed.
- Make sure automatically keep my Mac up to date is checked.
- Click Advanced and make sure the following boxes are checked.
- Check for updates.
- Download new updates when available.
- Install macOS updates.
- Install app updates from the App Store.
- Install system data files and security updates.
Contact your IT team as soon as possible if your work-issued computer was involved in the malware attack. Consider hiring an expert to help you with this process if you’re unsure of how to run anti-virus software or whether your computer has been completed cleared of malware.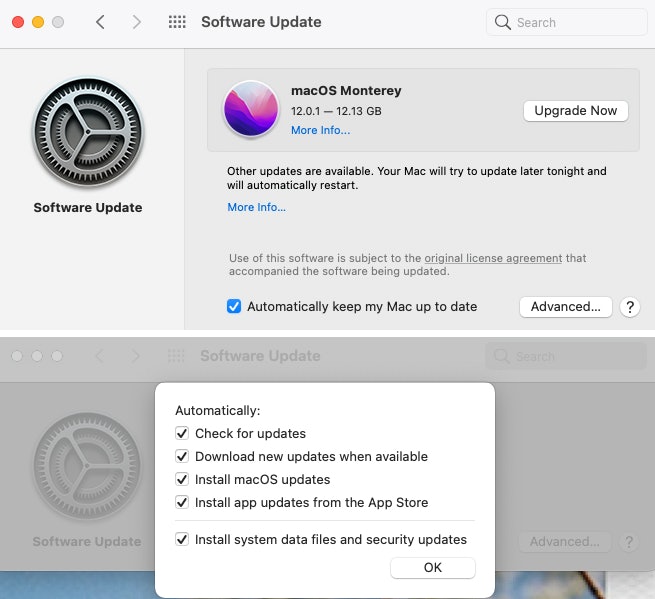
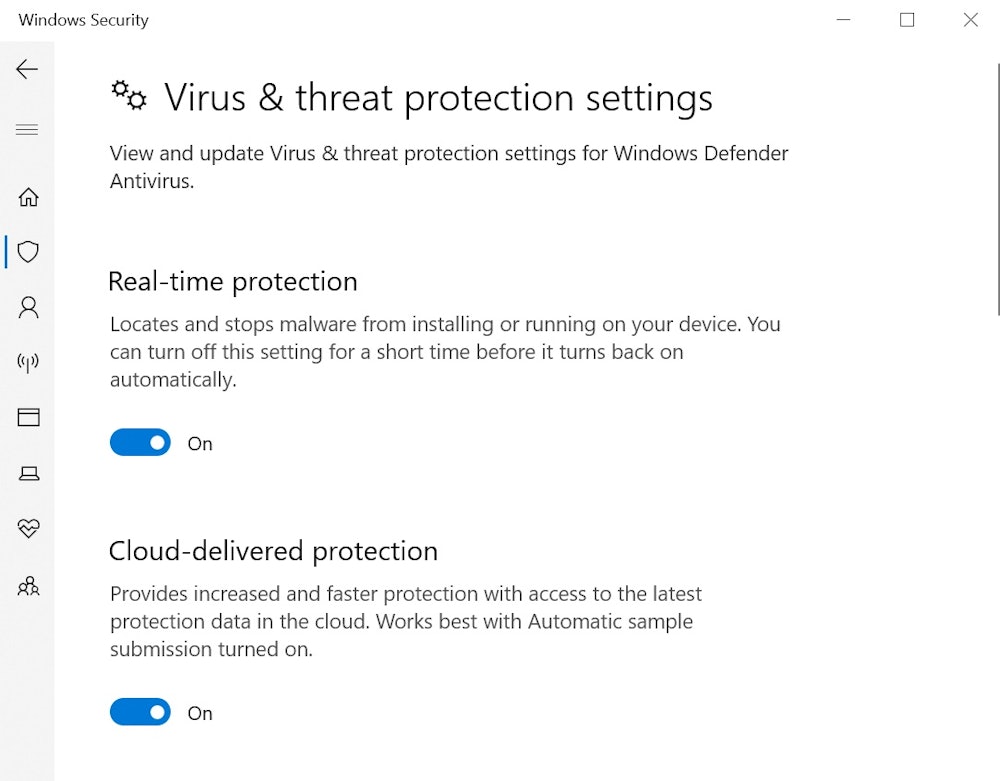
How to Run an Anti-Virus Scan
To perform a quick scan on Windows 10:
- Click on the Start menu.
- Type "Windows Security" in the search box.
- Choose Windows Security Settings.
- Click on Virus & Threat Protection.
- Under Current threats, select Quick Scan.
To perform an advanced scan on Windows 10:
- Follow steps 1-4 above.
- Click on Scan Options.
- Choose between a full, custom, or Windows Defender Offline scan.
- Click Scan Now.
The Windows Defender offline scan can be useful in the case of a malware attack. It will automatically remove any threats and restart your computer while disconnected from the internet.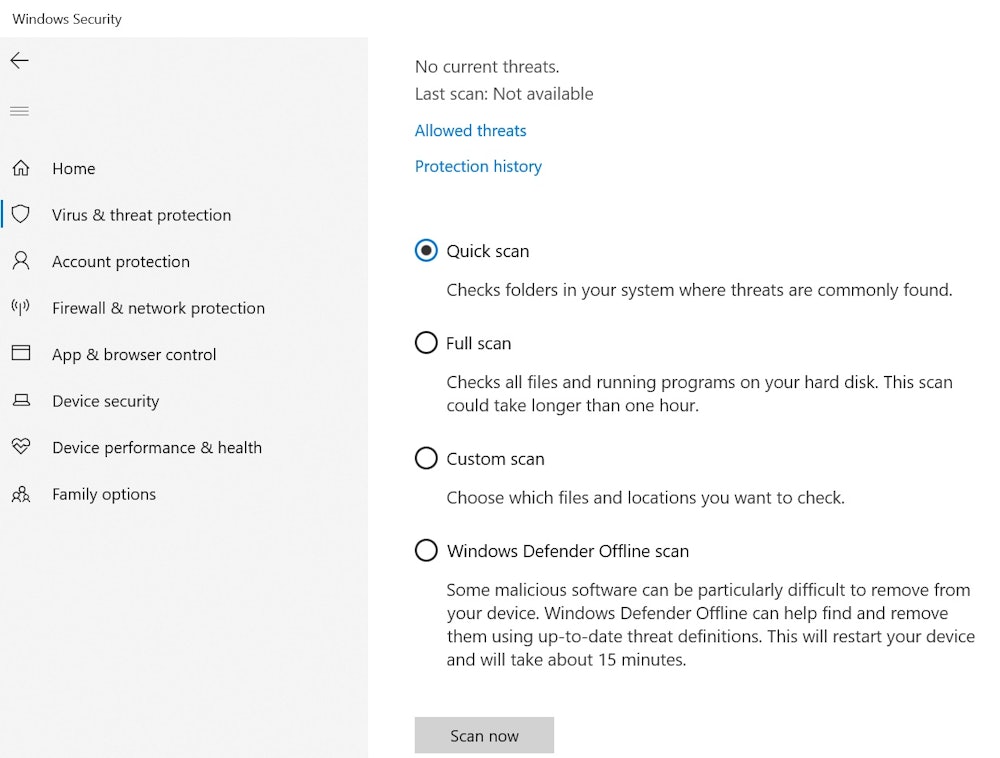
If you’re using a Mac, it will automatically scan for viruses and malware. However, to ensure you’re protected against unwanted applications launching, do the following:
- Click on System Preferences.
- Choose Security & Privacy.
- Click on General.
- Unlock the preference pane by clicking the lock icon.
- Enter your computer’s password.
- Under Allow apps downloaded from, check the box for App Store and identified developers.
- Click the lock icon once more to lock your preferences in.
Third-Party Anti-Virus Software
For additional protection, consider purchasing third-party anti-virus software for an extra layer of safety. Every day, new malware and online viruses are finding their way into our systems.
Thousands of Pieces of Malware Created Daily
The AV-Test Institute registers over 350,000 new pieces of malware and potentially unwanted applications (PUA) every day.
After installing the program of your choosing, be sure to follow step-by-step instructions on how to run a full scan and which security features you’ll need to turn on.
Step 4: Back Up Your Files
Without reconnecting to the internet, take the time to back up your files since data can be lost when trying to recover from a malware attack. Ensure you’ve run a scan and cleaned your computer of any malware first.
If you maintain your backups already via a cloud storage service, USB thumb drive, or an external hard drive, you should only need to do this for new files since your last backup. If you’re short on time, focus on any sensitive documents or files as well as irreplaceable records like family photos and videos.
How to Back Up Your Files
There are many ways to back up your files on your computer. The two most common ways are:
- Backing them up on an external hard drive
- Backing them up on the cloud
External Hard Drive Backup
This is the cheapest and easiest way to backup your hard drive. Using an external hard drive or a USB flash drive is typically the most traditional way of doing so. However, you’ll need to continuously backup your computer since the drive will only contain the items from your last backup.
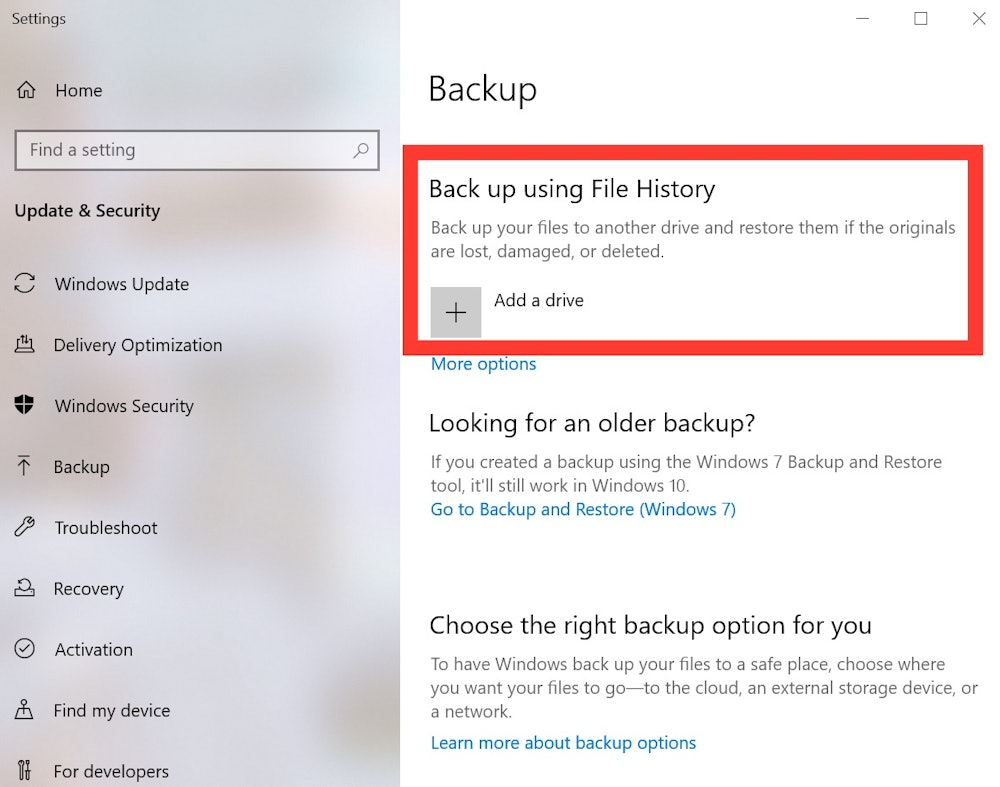
To backup your data on Windows 10 with an external drive:
- Insert your external hard drive.
- Select the Start menu and type "backup."
- Select Backup settings.
- Under the Backup using File History section, select Add a drive.
- You’ll be taken to a Select a drive popup with all external drives you have connected to your computer. Select the external drive you want.
- This enables the Automatically back up my files function showing a default list of files and folders most users want saved. To add others, select More options under the toggle.
- Review the folders under Backup these folders. If any are missing, select Add a folder or Remove to delete them from the list.
To back up your data on a Mac with an external drive:
- Insert your external hard drive.
- Locate System Preferences in the Apple Menu.
- Select Time Machine.
- Select Backup Disk.
- Select Your Hard Drive and Encrypt Backup.
- Create a Password for Your Backup.
- Wait for Backup to Begin.
Cloud Backup
Cloud backup is one of the best backup methods available and it allows you to access your files from anywhere, as long as you have an internet connection. Online cloud services are more costly than external hard drives since they often charge a monthly or yearly fee in exchange for storing your encrypted data.
To create a Google Drive backup for Windows:
- Download and install the Backup and Sync utility.
- Launch app and sign into your Google account.
- Click the Backup and Sync icon in your System Tray, followed by the three-dot Menu > Preferences.
- Go to the My Computer tab, choose which folders you want to backup. Choose Folder
- Click the Change button to decide if you want to backup all files, or just specific ones. Under Advanced settings, you ignore files with certain extensions.
- Backup and Sync should now be active. Enable Open Backup and Sync on system startup on the Settings tab so it runs automatically on startup.
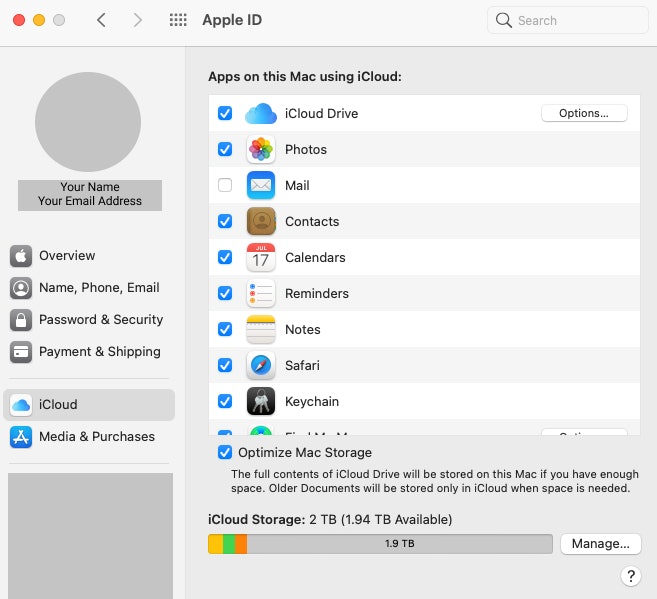
To create an iCloud backup for Mac:
- Go to the Apple menu.
- Click System Preferences, then click Apple ID.
- Select iCloud.
- Sign in with your Apple ID.
- Make sure the iCloud Drive box is checked as well as any applications that you want backed up.
- Click Options next to iCloud Drive to add additional documents.
- Hit Done.
Step 5: Review Your Financial Accounts
It’s important to review your financial accounts after a malware attack, especially if you mistakenly gave out sensitive information or your passwords were compromised. Once you’ve canceled your credit cards and reported any fraudulent charges, keep an eye on your accounts to monitor any suspicious activity. Here’s what to do:
- Call your credit card company immediately and cancel your card(s).
- Notify the credit bureaus.
- Set up fraud alerts.
- Monitor your statements and credit reports.
How to Cancel Your Credit Cards
To cancel your credit cards, call the corresponding financial institution immediately. This could be your bank, credit union, or credit card companies such as Discover and American Express.
There should be a customer service number on the back of your card to call for assistance. Follow the phone prompts to report fraudulent charges and speak with a representative regarding your accounts. You may also go in person to your bank and speak with someone in person who can help you cancel your cards and order new ones.
How to Report Fraudulent Charges
It’s essential to report a stolen credit card or fraudulent charges immediately. According to the FTC, if there are unauthorized transactions using your debit card number and your card isn’t lost, you’re not liable for the transactions. However, you must report it within 60 days.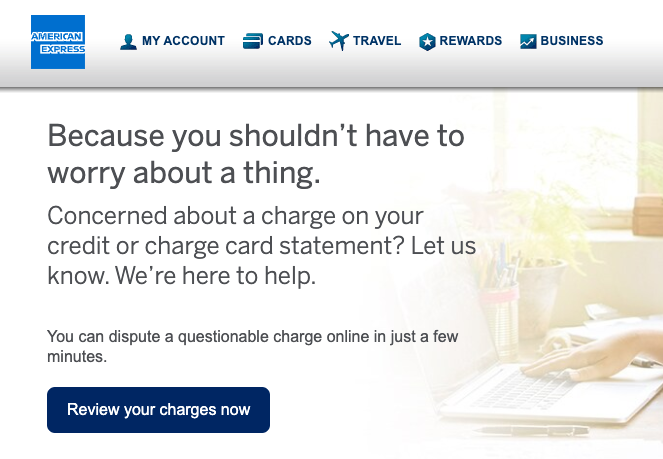
To review and report fraudulent charges, call the number on the back of your card to speak with a representative. Or, type “how to report fraudulent charges on [cc name]” into your internet browser. Be sure you’re using your card’s actual website when looking for step-by-step instructions. It should be a secured site and start with “https:” in the URL.
Freeze Your Credit
If you gave your Social Security number to the scammer, you'll want to freeze your credit or place a fraud alert on your credit report.
There are three major credit bureaus you’ll want to notify of the incident: Experian, Equifax, and TransUnion. Contact each and request a credit freeze to avoid cyber criminals from doing damage to your credit score. A credit freeze restricts access to your credit report so that no accounts can be opened during this time—by you or the cybercriminal.
- Experian: (888) 397-3742
- Equifax: (888) 298-0045
- TransUnion: (888) 909-8872
Set Up Fraud Alerts on Your Credit Report
There are two alerts you’ll want to set up on your accounts: initial and extended alerts. Initial fraud alerts will place an alert on your file for one year. After that, it will be removed and you can choose whether you’d like to sign up for another year.
These fraud alerts require creditors to take reasonable steps to ensure any new credit requests are made by you. You’ll also be entitled to one free credit report from each company which doesn’t count against your one free yearly report.
How Long Do Fraud Alerts Last?
- Initial fraud alerts: This type of fraud alert lasts for 1 year and can be renewed each year after.
- Extended fraud alerts: This type of fraud alert lasts for 7 years.
Extended fraud alerts are good for seven years and require the creditor to contact you in person, via phone, or another designated method to verify that a credit request is done by you. It also entitles you to two free copies of your credit report from each credit reporting company over a 12 month period.
To set up fraud alerts, call each of the credit reporting companies above.
Step 6: File a Report With the FTC
Finally, report the malware attack to the Federal Trade Commission (FTC) to help them combat the scammers as well as the FBI.
- Report the malware attack to the FTC at ftc.gov.
- Report it to the FBI’s Internet Crime Complaint Center.
Step 7: Contact the Impersonated Company
Finally, it’s a good idea to alert the company that was being impersonated of what occurred. Give them all the details as well as any photo or video evidence you may have; they will likely want to investigate the matter and make sure no one else was affected.
Ask if there are any other security measures you can take on their site for safeguarding your information and account. If you gave out financial information for a credit card, you may need to cancel your existing one while on the phone with them.
Step 8: Stay Vigilant
Finally, now that you’ve taken all the necessary precautions to protect your identity, it’s important to continue to monitor your accounts and watch out for future malware attempts.
How to Monitor Your Accounts
- Download a mobile banking app to access your accounts at any time of day.
- Set up alerts for your bank accounts and credit cards via text and/or email to be notified of any suspicious transactions, failed login attempts, or changes to your personal information.
- Consider a mobile budgeting app to connect your checking, savings, and credit card accounts in order to see all of your account activity at once.
- Add a reoccurring reminder in your calendar to review your online statements each month.
How to Avoid Malware
- Only install well-known software directly from the source. Sites offering popular software for free are more likely to include malware.
- When installing software, read each screen before accepting. If you’re asked to install bundled software, exit the installation process or decline the additional program.
- Don’t ignore your browser’s security warnings. Many come with built-in security scanners that alert you to webpages that may be infected or malicious.
- Type the URL of a suspicious link in your browser instead of clicking on it to see if it is a real link. Often, if it is an infected link, user reports will pop-up in the search results.
- Don’t click on pop-ups regarding your computer’s performance or security being out-of-date. Scammers can insert unwanted software into these messages to trick you.
- Scan all external devices before using them to make sure they aren’t infected with malware.
*Disclaimer: Some operating system processes may vary dependent on your computer. Call your device's support team should you need additional assistance.









Comments