- What Did The Hackers Want?
- What Has Been Exposed in the Optus Data Breach?
- What Has Optus Done Since The Attack?
- How Can I Protect Myself?
- Frequently Asked Questions
On the 22nd September 2022, one of the largest telecommunications companies in Australia, Optus, reported that hackers had gained unauthorised access to the personal information of current and former customers in what is now widely known as the Optus data breach.
Optus advised that the information which may have been exposed includes customers’ names, dates of birth, phone numbers, email addresses, and, for a subset of customers, addresses, ID document numbers such as driver's licence, medicare number or passport number. They also advised that payment detail and account passwords had not been compromised.
Gomo, Prepaid and Postpaid Optus Mobile, Personal Optus Broadband, and Optus Business (SMB) customers from 2017 onwards have been affected. This includes current and former Optus customers, so even if you no longer have an active account with Optus, your personal information may still have been exposed in the Optus data breach.
Optus have shut down the unauthorised access, but it was estimated that up to 9.8 million customer records had been exposed and likely downloaded by the hackers, making it one of the largest cyberattacks in Australian history.
What Did The Hackers Want?
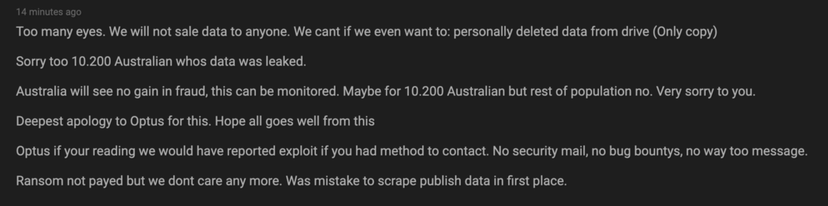
Shortly after Optus released information of the hack to the media, the alleged hackers posted to an online forum demanding that Optus pay US$1 million in cryptocurrency as a ransom to prevent them from releasing the customer information to the internet. The hackers also released a small sample of 200 records to prove they were in possession of the data.
A couple of days after their initial demands, the hackers released a further 10,000 records and vowed to continue releasing data daily unless their ransom was met.
However, within hours of posting this demand online, the hackers posted another message to the online forum apologising for their actions and vowing not to continue releasing the stolen data. They promised not to sell the data and claimed to have deleted the only copy of the data from their drive.
What Has Been Exposed in the Optus Data Breach?
When you sign up for an Optus product, you need to provide proof of identification in the form of a driver licence, passport or medicare details in order to complete the purchase.
Depending on what form of identification you provided to Optus, the following information may have been exposed to the hackers:
- Name
- Address
- Date of birth
- Phone number
- Email address
- Driver licence details
- Medicare details
- Passport details
Driver License
Some states issue driver licences which include a licence number and a card number, while other states only issue cards with a single licence number.
From 1 September 2022, NSW, Western Australia, the ACT, South Australia, Tasmania and the Northern Territory adopted new rules required to pass a national Document Verification Service (DVS), which is used to verify a person's identity.
Under the changes, all driver licences issued in those states that are used in ID checks require both the licence number and the card number to complete the verification process.
Any Optus customers who signed up before 1 September 2022 will not have provided their card number so this information has not have been exposed to the hackers. Without both numbers, hackers will not be able to verify your identity using your licence number alone. However, for Victoria and Queensland licence holders, you will need to request a new licence number.
Medicare Card Number
Optus have identified 17,000 valid Medicare ID numbers that have not yet expired and a further 26,000 expired Medicare numbers that have been exposed.
If you provided your Medicare card details to Optus as part of the identification process, you are strongly encouraged to replace your Medicare card. You can do this through:
- Your Medicare online account at myGov
- Express Plus Medicare mobile app
- Calling the Medicare program on 132 011 (24/7)
What Has Optus Done Since The Attack?
Optus has now sent email or SMS messages to all customers whose personal information has likely been compromised as part of the data breach.
They have established a dedicated section on their site to provide information for customers who may have been affected by the Optus data breach with the latest updates and important resources to help you mitigate any personal risks.
https://www.optus.com.au/support/cyberattack
Optus have also offered a free 12-month subscription to Equifax Protect to the most affected current and former customers. Equifax Protect is a credit monitoring and identity protection service that can help reduce the risk of identity theft.
How Can I Protect Myself?
Regardless of whether your information was exposed as part of the Optus data breach, it's important to always remain vigilant about any unsolicited emails, text message and phone calls.
Being educated about techniques that scammers and hackers use is also an important defence against becoming a victim of a scam.
Here are some simple tips to staying safe from scammers and hackers:
- Never click on any links in emails that you are not familiar with or that look suspicious
- Never respond to requests to provide personal or account information
- Never provide passwords, personal or financial information
- Never provide remote access to your device if requested
- Monitor your online accounts for any suspicious or unexpected activity and report such activity immediately
- Wherever possible, use two-factor authentication (2FA) / multi-factor authentication (MFA) for all your accounts
- Monitor your credit report for any new credit applications in your name
- Signup for a service like CreditSavvy or Equifax Protect that will notify you when there is any activity on your credit file
- Apply for a credit ban with Equifax, illion and Experion to prevent enquiries on your credit report and prevent new applications for credit under your name. CreditSavvy offer a service called SavvyShield that allows you to quickly apply a credit ban across all three credit agencies


Comments