
Most Read

What is Extortion? An Easy to Understand Definition

How to Beat Bitcoin Blackmail Emails & Protect Yourself

How to Tell if Nikes Are Fakes: From Tags to the Stitching
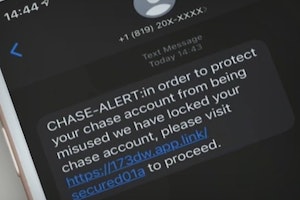
Real Chase Fraud Text Alert or Scam Message?
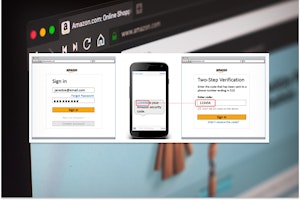
Received an Amazon OTP Text? It Could Be a Scam
Threats & Extortion In Depth
- Common Scams Involving Threats and Extortion
- Red Flags of Threats and Extortion
- How to Beat Threats and Extortion
- Fallen Victim to a Threat or Extortion?
Sometimes scammers try to hook you with the promise of winning money and prizes. Unfortunately, they also do the opposite, using threats and intimidation, which can be even more effective.
In a recent report by the FBI, threat and cyber extortion scams were the third most common types of online fraud in the United States. These attacks attempt to take advantage of people of all ages, seeking to scare them into providing money or login credentials.
Threats and extortion come in a variety of forms. But the intended result is always the same—to quickly intimidate a victim, get money or steal sensitive information, and then disappear. While these attackers can be elusive, there's a lot you can do to protect yourself, especially when you know how this kind of fraud works, red flags to look out for, and how to beat these scammers.
Common Scams Involving Threats and Extortion
Threats and extortion scams seek to pressure people into paying money or providing sensitive information. Cybercriminals use one or multiple threats to get the target to make an emotional decision.
Threats and extortion scams have been very successful in recent years. For example, the state of Montana alone had 186 victims of extortion in one year, with victims paying, on average, $2,221 per account.
The most common forms of threats and cyber extortion are communications that appear to be from legitimate organizations and those that threaten to expose images or videos of a sexual nature, also referred to as sexploitation.
Scammers Tricks
- They send you a message claiming that they have accessed your files or other personal information.
- They threaten to release the information if you don't pay them cryptocurrency.
Sextortion and Blackmail
A sextortion attack typically begins with an email from the attacker saying they have footage of you in a compromising position. It could be anything from videos of you doing sexual things online, a list of your browsing history featuring visits to pornographic sites, to explicit photos.
The criminal will say they're going to publish the content online if you don't pay them a fee, often using cryptocurrency since it's impossible to track. They don't have anything on you in most cases, and they're simply after your money.
Sextortion can even target young children.
Imposters
Scams where the attacker pretends to be from a legitimate company or government agency work like this:
- The attacker collects details about the company/agency online, using them to craft a convincing email or make them sound legitimate over the phone.
- They claim you owe their organization money, and you face severe penalties, such as legal action or even arrest.
- They ask you to make payment via a method that's hard to trace, such as with a gift card, store card, or cryptocurrency.
- Once you pay, they disappear.
In some cases, they may ask you for identity or account information during the attack. Even though you don't pay them money, they can still profit from selling this to someone else or using it to steal your identity.
It's common for these scammers to impersonate:
- The Federal Bureau of Investigation (FBI)
- The Internal Revenue Service (IRS)
- The Central Intelligence Agency (CIA)
- Customs and Border Patrol
- Well-known companies (e.g., Apple)
Targeting Immigrants
At times, a scammer may try to take advantage of someone from another country, telling them they will be deported unless they follow specific instructions. The instructions will likely include a payment request, but they may also ask for contact information, passwords, or user credentials.
Cyber Extortion
Cyber extortion is where a hacker or group of hackers hold a company's data, systems, or private information (like customer details) for ransom until they are paid. These attacks use ransomware, typically sent out via links in phishing emails to employees.
When someone clicks on the link, the hackers access company systems and infect them with viruses.
There are two main types of ransomware:
- Locker: Locks users out of their accounts until a ransom is paid
- Crypto: Encrypts data on a company's servers, and hackers hold a key that they won't release until a ransom is paid.
Sometimes if they have managed to steal sensitive information like credit card details, they threaten to release it online. This kind of extortion is large-scale—payment demands can be in the millions of dollars.
Red Flags of Threats and Extortion
In many cases, a threat or extortion scam is relatively easy to spot, mainly because of how the attacker tries to leverage fear during the interaction. For example, any time you get a phone call, email, or text that says something terrible will happen if you don't pay money, it may be a scam. This includes communications that seem to be from legitimate businesses you've dealt with in the past.
Threats to Expose Information or Files
If you ever get an email that threatens to expose your online photos, videos, or history if you don't pay them, you should assume it is a scam. In many cases, they may not even have any of this information—they often send out a blanket email to several different people, hoping one or a few would take the bait.
Threats From a Company or Government Agency
Another red flag is if you get a call, email, or text message that appears to be from a company, the police, or a government official or agency, saying you'll have to pay a hefty fine if you don't pay a smaller amount right away. Again, this is typically a scam. In all cases, you can reach out to the actual company or agency the person claims to represent to verify the legitimacy of what they're saying.
Unsolicited Calls from Law Enforcement/Government Requesting Money
If someone from law enforcement or a government department calls you requesting money, it's likely a scam. For example, if you owe money to the IRS, they will send you a letter with information—they won't call you and tell you to pay up.
Additionally, law enforcement will never call you asking for payment to get you out of an arrest warrant. If you have an arrest warrant, they will just come and arrest you—they won't call you to give you an out.
Requests for Payment via Unconventional Methods
If the person you're speaking to requests payment via any of the following methods, it's likely a scam:
- Cryptocurrency
- Wire transfer (e.g., MoneyGram)
- Gift cards
Scammers only want you to pay using methods that can't be traced back to them and can't be reversed.
How to Beat Threats and Extortion
To beat threats and cyber extortion attacks, remember these tips:
- Ask for the person's name and tell them you'll call back. Then, call them back using the company/department number you find online and ask to be transferred to them.
- Never provide any payment or information to someone who claims something terrible may happen if you don't.
- Don't believe calls from law enforcement (e.g., the FBI) claiming you risk being arrested unless you pay money.
- Don't believe anyone who asks for payment via non-conventional methods.
- Even if it seems like you're dealing with a legitimate collection agency or government organization, do not provide any info or payment unless you can verify the legitimacy of the call or email.
- Keep all your files safe by using a virtual private network, anti-virus software, and anti-malware software.
- Don't click on any links or open any email attachments unless you can verify it is from a safe sender.
- Don't use public WiFi when accessing sensitive information or files.

- Malware and adware blockers.
- Secure 6 devices at once.
- 30-day money-back guarantee.

- Military-grade encryption.
- Protection for unlimited devices.
- Allow specific sites to bypass VPN.

- Find the fastest server in your location.
- Use on up to 5 devices.
- Robust data encryption.
Fallen Victim to a Threat or Extortion?
If you've fallen victim to a threat or extortion scam, you should report it to:
- The FBI
- The company or government agency they were impersonating
- Your local police
If you've sent money to someone using a cryptocurrency exchange or a gift or store card, you may be able to prevent the payment from going through before they claim the funds. Contact the card-issuing company or the crypto exchange and explain the situation. However, in most cases, the scammer will claim the money immediately, so you don't have time to reverse it.
Scams Relating to Threats & Extortion

How to Beat Bitcoin Blackmail Emails & Protect Yourself
If a hacker is blackmailing you to get bitcoin, it can be hard to figure out if it's an empty threat or a real one.
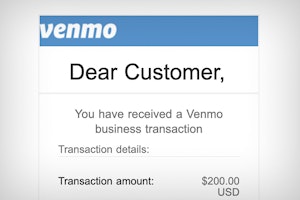
Selling on Facebook Marketplace? Beware of Fake Venmo Emails
Scammers are sending fake Venmo emails to Facebook Marketplace sellers in an attempt to steal login information and money.

Citibank Text Message Scam: Locked Debit Card Alert Is Fake
If you've received a locked debit card text message from Citibank, it's likely a scam. Don't click on the link and delete the text message.

Real Chase Fraud Text Alert or Scam Message?
If you receive a text message from Chase Bank, don't click on any links or call the phone number listed—it could be a scam designed to steal your information and money.
Amex Fraud Text Alert Scams: Spotting a Fraud
If you receive a text message from American Express, don't click on any links or call the phone number listed—it could be a scam designed to steal your information and money.

Fake Verizon Text Messages: How to Avoid a Scam
Verizon may send you text messages from time to time with account updates or data usage alerts, but beware—most of these aren't really from Verizon but scammers.

Get an Unexpected Delivery Alert? It May be a UPS Text Scam
Scammers are using SMS messages to send fake alerts to customers regarding a package delivery. Here's what to know about this scam.
Venmo Text Scam: Don't Fall For These Fake Messages
If you received a text from Venmo with a link to verify a payment or deposit, or are asked to complete a survey in exchange for money, it may be a scam.

Truist Text Alert: How to Identify a Real Text from a Scam
You may think that that Truist have sent you a text alert about your account. Here's how to check if it is actually a scam.

Wait! That Walmart Giveaway Text May be a Scam!
Fake texts are being sent to consumers claiming a hefty sum is waiting for them on a Walmart gift card, but falling for this scam puts you at risk of identity theft.
Guides Relating to Threats & Extortion

How to Get Verified on TikTok
Securing that little blue checkmark can mean brand collabs, sponsorship opportunities, or protecting your unique content from impersonators.

How to Tell if Nikes Are Fakes: From Tags to the Stitching
Nike is one of the biggest brands targeted by counterfeiters and scammers - be extra careful with Nike products from non-official retailers as you could end up with a fake

Funeral Homes & Prices - What Are The Costs & Your Rights?
Average prices from funeral homes range between $8k to $14k and consumers are meant to be protected by a 'Funeral Rule' - what are your consumer rights?

How to View Your Amazon Archived Orders & Hide Search History
If you share your account with multiple users, archiving your past orders is a good way to keep others from seeing your orders and ruining a surprise or seeing private orders.

The Dangers of Fake THC Vapes Flooding The Market
If the health dangers surrounding vape cartridges weren't bad enough, fake THC vapes containing harmful contaminants are being sold.
News Relating to Threats & Extortion

Urgent CDC Warning: Eye Drops Linked to 3 Deaths, Loss of Vision
The CDC is warning eye drops users of a rare bacterial infection from 2 brands of eye drops. The infection is resistant to antibiotics and has resulted in the loss of vision, loss of eyeballs and the death of 3 patients.

Banks May Refund More Zelle Scam Victims in 2023
Zelle scams have reached a serious volume. New reports suggest that banks are looking at new refund protections for customers in 2023.

Optus Data Breach - One of the Worst Cyberattacks in Australia
Hackers have gained access to 9.8 million customer records from Optus in Australia, exposing personal information such as driver licence, medicare and passport details.

Roe vs. Wade Overturned: Abortion Rights in Your State
Find out what the overturning of Roe vs. Wade means for abortion rights in your state.
Searches for "COVID Vaccine 5G" Hit All-Time High, But Microchips Definitely Not in Vaccine
The number of people searching for the term "COVID vaccine 5G" on Google has just hit an all-time high, but there's one way to be sure that there are no microchips.