Identity Theft In Depth
- What Is Identity Theft?
- The Goal of Identity Thieves
- Red Flags of Identity Theft
- How to Beat Identity Theft
- Most Common Types of Identity Theft
- Have You Fallen Victim to Identity Theft?
- How to Report Identity Theft
Identity theft is been on the rise, with losses totaling $712.4 billion in 2020—42% higher than in 2019. Even though the most common victims are those between the ages of 35 and 44, virtually anyone can become a victim.
Complaints about identity theft have risen faster than those regarding general fraud, as well as other consumer complaints, with a 45% increase from 2019 to 2020. In many cases, identity thieves are out for financial gain, using their targets’ information in an attempt to steal their money.
And in some cases, the thief will take someone’s identity and sell it to someone else—either as part of a package or on its own.
What Is Identity Theft?
Identity theft is a tool criminals use to gain access to sensitive accounts or to impersonate their victims, often to make or steal money. Thieves and scammers may try to attain just enough information to enable them to take their victim’s funds or abuse their credit, or they may obtain a complete identity profile, enabling them to execute multiple types of fraud.
How Does Identity Theft Work?
The first step an identity thief takes is stealing your personally identifiable information (PII). They can accomplish this in a variety of ways, including:
- Hacking devices
- Breaking into online user accounts
- Fooling you into giving away personal data
- Going through your trash
- Intercepting your mail
- Breaching a computer or server that stores your information, often along with that of many others
After the thief has obtained your information, they then use it to levy various kinds of fraud, such as accessing financial accounts, making withdrawals, or taking them over completely, as well as making purchases or opening lines of credit.
Thieves can also use personally identifiable information to file fake tax returns, acquire sensitive documents like passports or health insurance cards, or rent vehicles and steal them.
According to the non-profit organization, Identity Theft Resource Center (ITRC), there were 1,291 breaches from January to September 2021. During these attacks, criminals hope to glean as much PII as possible—and then use it to execute their plan.
A single breach can uncover thousands of identities, especially because many companies store sensitive information gathered from their clients, such as credit card or banking information, the names of relatives, and current and former addresses, phone numbers, and email addresses.
The Goal of Identity Thieves
Typically, the ultimate goal of identity theft is to make money. But this isn’t always the case.
For example, sometimes thieves can steal your picture to conceal their own identity, often using your social media account.
In this type of fraud, the bad actor may go to your social media account, copy several of your pictures, and then use them as their own while opening their own account.
They can use this same tactic for the usual reason: to make a profit. For example, the thief can create an account using your name and pictures and then reach out to one of your Facebook or Instagram connections. They then pretend to be you and try to trick the person into giving them money.
Red Flags of Identity Theft
There are some easily identifiable red flags that may indicate you’ve been a victim of identity theft:
- Receiving debt collection letters or phone calls for accounts that you never opened or see inaccurate info on a recent credit report.
- Getting denied when applying for credit because the thief illegally used your credit without paying the money back.
- Noticing odd transactions in your bank account or on your credit statement, such as purchases you never made.
- At times, victims may start getting suspicious bills, either in the mail or via email, because the thief purchased a good or service using their information.
- A data breach at your company or one you do business with.
One of the biggest red flags is when there’s been a data breach at the company you work for or ones you do business with, such as a retailer or credit card company, or on your personal device. Even though you may not notice any suspicious activity right away, the thief may have sold your data to another malicious actor who may be waiting for the right opportunity to defraud you.
How to Beat Identity Theft
If you’re aware of someone trying to steal your identity, you should refuse to provide them with any personal information, such as your credit card number, banking info, or social security number.
You should also avoid clicking any links in an email asking for personal information because the link could install malware on your device that can be used to steal personal information.
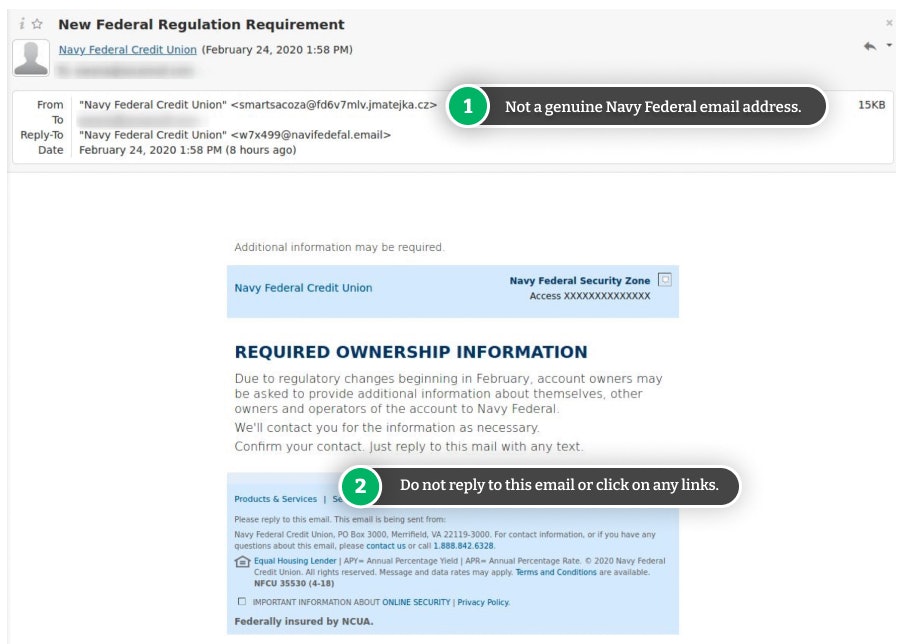
At times, you may suspect someone may be trying to steal your personal data over the phone or via email. Even if it seems like they’re from a legitimate company, you should double-check their validity.
For example, you can ask for the company’s phone number, call it, and ask if the caller really works for them. You can also hover over the sender’s email address with your mouse to see if it’s from a legitimate site.
Most Common Types of Identity Theft
The most common types of identity theft include:
- Financial: This type of theft occurs when someone steals your financial info for personal gain
- Tax: This type of theft occurs when someone pretends to be you to get a tax refund
- Medical: This type of theft involves a thief using your information to get medical care
- Employment: This type of theft involves a thief using your personal information to get a job
- Child: This type of theft involves thieves using a child's name to open lines of credit
- Senior Citizen: This type of theft occurs when the thief specifically targets an older person
David Putnam, Head of Identity and Insurance Products at NortonLifeLock, says that it's not just computers we need to be careful with. "Cell phones can be just as vulnerable—if not more—than your computer, depending on how often you use it and what you store on the device," he says.
"Many people nowadays use their cell phones as a personal computer, meaning it has significantly more data and personal information than it did 20 years ago," Putnam adds. He warns that several things can be exposed from your cell phone, including your:
- Photos
- Call data
- Text messages
- Physical location
- Bank records
- Health data
Have You Fallen Victim to Identity Theft?
If you’ve fallen victim to identity thief, there are a few steps you can take to recover from the compromise:
- Contact your credit companies to freeze or cancel your accounts
- Contact your bank to alert them of the incident
- Place fraud alerts on your credit report
- Freeze your credit
- Report it to the authorities
- Change your passwords, especially if you use the same one for multiple accounts
Taking these steps enables you to cut off the thief’s access to your money and credit. You should then check your financial statements and continue to monitor them for any suspicious activity.
What to Do If the Thief Has Stolen from You
If the thief has stolen money from an account or run up bills in your name, you may be able to recover your funds. Promptly contact the financial institution associated with the account they used and let them know what happened.
If the malicious actor used your identity to purchase something online, you may be able to recover your funds by contacting their customer service or fraud department directly—via phone, email, or live chat.
How to Protect Yourself from Identity Theft
Follow these dos and don’ts to protect yourself from identity theft now and in the future and check out our guide to the best identity theft protection services.
Do
- Check your credit reports for unusual activity. You can order your credit reports for free once a year.
- Collect your mail every day and put a hold on your mail when you’re away from home for more than a few days.
- Monitor your billing cycles. If bills or financial statements are late, contact your provider as soon as possible.
- Use the security features on your phone and other devices, and ensure you have the latest version of the software.
- Stay up to date on the latest scams, especially phishing scams designed to steal your sensitive information.
- Shred receipts, account statements, expired credit and bank cards, and credit card offers, to prevent “dumpster divers” from stealing your personal information.
- Use a virtual private network (VPN) when using public WiFi.
Don’t
- Use the same password for all your accounts. Instead, create unique passwords with a mix of letters, numbers, and symbols.
- Carry your Social Security card in your wallet and only give out your SSN when necessary.
- Neglect to review your credit and bank account statements for unauthorized transactions.
- Share personal information or carry out financial transactions on public WiFi, unless you're using a virtual private network (VPN) to keep your data secure.
- Store personal information and statements in an unsafe place.
How to Report Identity Theft
If you discover you’ve been a victim of identity theft, you should report it on the U.S. government’s identity theft website. Provide them with all the details you have, including communications or any suspicious activity you’ve noticed. They may be able to use the info you give them to apprehend the thief, which can make it easier for you to get your money back.
It may also be helpful to report the theft to the police. Do this sooner than later to potentially help protect yourself from further damage. Additionally, there are various organizations that you can report it to, depending on the type of account that was used.
| Type of Account | Who to Report it To |
| Phone | National Consumer Telecom and Utilities Exchange (ask for your data report) |
| Social Security Benefits | Social Security Administration |
| Student Loans (Federal) | U.S. Department of Education |
| Tax Fraud | Internal Revenue Service |
| Utility (e.g., water, electricity) | Your State's Public Utility Commission |
Scams Relating to Identity Theft

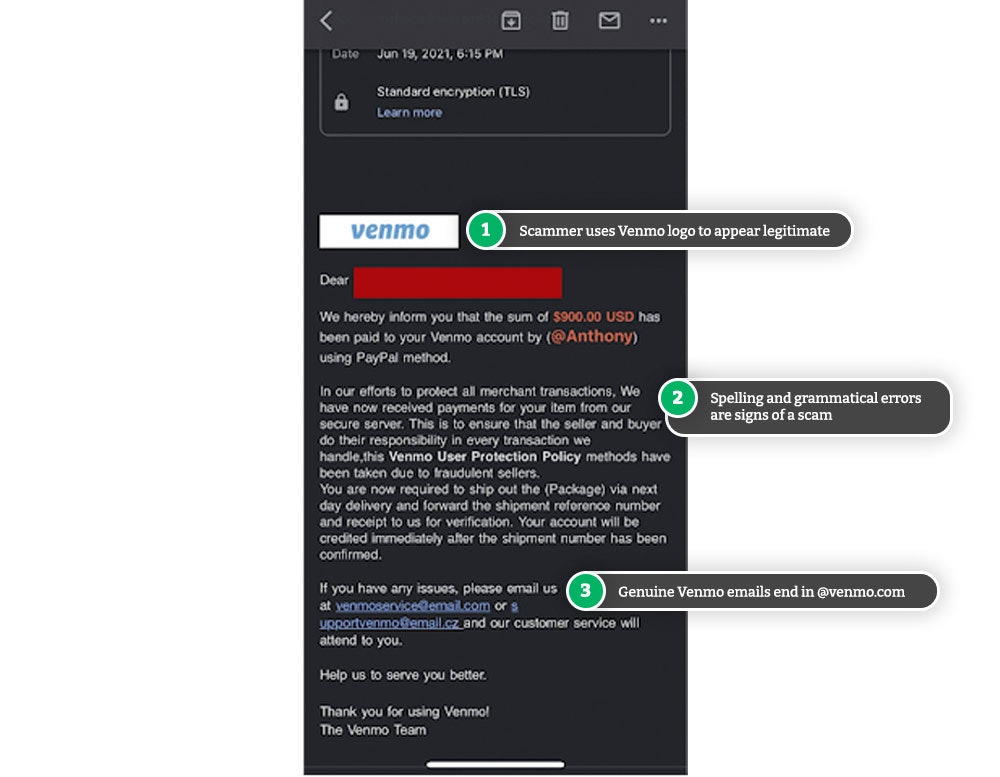
Venmo Email Scams: Red Flags & How to Beat Them
Venmo users are noticing suspicious emails hitting their inboxes with claims of a large sum of money waiting to be transferred by a PayPal user.

Unemployment Fraud: How It Works & How to Stay Safe
As unemployment claims rose higher than ever in 2020, so did cases of unemployment identity theft.

Apple Support Scam: Beware of Callers Impersonating Apple
If you receive a phone call from Apple Support, it could be a scammer attempting to steal your information and access your accounts.

SIM Swap Scams: How to Stop Your Phone From Being Hijacked
Losing your cell phone isn't the only way your information and data can be stolen—scammers can steal your phone number and info without you even realizing it.

Beware of Magazine Subscription Scams Asking for Payment
Scammers are tricking people into thinking they're paying for subscriptions they don't want, in an attempt to steal your information and money.

Dangerous Netflix Scam Emails: How to Identify & Beat These 'Netflix Suspension' Scams
That Netflix email may seem genuine, but be sure to look for any red flags of a scam so you don't fall victim to identity theft.
Selling on Facebook Marketplace? Beware of Fake Venmo Emails
Scammers are sending fake Venmo emails to Facebook Marketplace sellers in an attempt to steal login information and money.

Citibank Text Message Scam: Locked Debit Card Alert Is Fake
If you've received a locked debit card text message from Citibank, it's likely a scam. Don't click on the link and delete the text message.
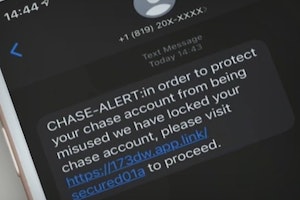
Real Chase Fraud Text Alert or Scam Message?
If you receive a text message from Chase Bank, don't click on any links or call the phone number listed—it could be a scam designed to steal your information and money.
Amex Fraud Text Alert Scams: Spotting a Fraud
If you receive a text message from American Express, don't click on any links or call the phone number listed—it could be a scam designed to steal your information and money.
Guides Relating to Identity Theft

Identity Theft Trends in 2023
Identity theft is a complex and evolving issue that requires collaboration and awareness from individuals, businesses, and policymakers. As the problem becomes more rampant, it is more important to be proactive in implementing the best solutions.
Identity Theft: The Best Identity Theft Protection Services
Over 1.4 million Americans reported being victims of identity theft in 2021. With the rapid rise of identity theft, it is now more likely that you will become a victim of identity theft than to have your car stolen.

How to Beat PayPal Scams and Keep Your Money Safe and Secure
Whether you use PayPal for personal use or business transactions, scammers are out to get you. It's what you know and how you act that will keep your money safe.

Health Insurance Spam Calls: What You Need to Know
Health insurance spam calls can be a nuisance, especially around open enrollment. But are they just annoying or potentially dangerous too?

How to Place an Experian Fraud Alert: Online, Call, or By Mail
Placing a fraud alert on your credit report is important when trying to recover from identity theft.
News Relating to Identity Theft

Optus Data Breach - One of the Worst Cyberattacks in Australia
Hackers have gained access to 9.8 million customer records from Optus in Australia, exposing personal information such as driver licence, medicare and passport details.

Urgent CDC Warning: Eye Drops Linked to 3 Deaths, Loss of Vision
The CDC is warning eye drops users of a rare bacterial infection from 2 brands of eye drops. The infection is resistant to antibiotics and has resulted in the loss of vision, loss of eyeballs and the death of 3 patients.

Banks May Refund More Zelle Scam Victims in 2023
Zelle scams have reached a serious volume. New reports suggest that banks are looking at new refund protections for customers in 2023.

Roe vs. Wade Overturned: Abortion Rights in Your State
Find out what the overturning of Roe vs. Wade means for abortion rights in your state.
Searches for "COVID Vaccine 5G" Hit All-Time High, But Microchips Definitely Not in Vaccine
The number of people searching for the term "COVID vaccine 5G" on Google has just hit an all-time high, but there's one way to be sure that there are no microchips.








